I’ve always been a fan of Netopia.
I’ve used Timbuktu remote control software since forever (1990) and we still use it today on our servers even with the availability of VNC and Apple Remote Desktop (I repeat myself).
Back in the early 90’s when ISDN connections were all the rage, at a previous employer, we used Netopia ISDN 440 Internet Routers extensively. We interconnected several branch offices in Texas to create an AppleTalk WAN using AURP (AppleTalk Update-base Routing Protocol). We had a hub and spoke system to create our own “VPN tunnels”, so the corporate office in Dallas could print to a Laserwriter printer in a branch office in Houston. It was cool stuff that was easy to setup. We also used those AppleTalk tunnels to interconnect first our QuickMail Servers using the AppleTalk ADSP File Transfer plugin for the Communnications Toolbox, then our AppleShare IP 5.0 mail servers taking an inbound SMTP over IP from our ISP connection then to an SMTP over AppleTalk to the specific branch office for that employee. One of the cooler features of that mail server and oh the heady days of the AppleTalk Network Browser.
So when Netopia came out with the R-series of routers for T1 and DSL deployments in the late 90’s, they were the old reliable friend updated for the latest technology. They were a bit outdated in their typical configuration with ony a 10mbit WAN port and an 8-port hub, but we usually downlinked that to a faster switch with more ports anyway and didn’t really need anything faster than 10 mbits total throughput anyway.
A year or two ago, when we needed to update two of our site to site VPN tunnels and support roadwarrior access from home to office and colo networks, we thought we would give them a try. We tried a R9100 at our office connected to an R9100 at the colo and while it was easy to setup, unfortunately, it was dog-slow.
We’ve since switched to using NetScreens, but since they have at LEAST one million different options, we’ve only really gotten the site to site vpn setup working and we really miss the very easy PPTP (especially for Mac OS X clients) VPN connections that the Netopia OS/firmware provides.
So when a customer recently asked about setting up VPN access into the backside network of their colo systems, I went back and looked at what the Netopia line had to offer. What I found was the 3386-ENT. Which turned out to be JUST what I was looking for: A 10/100 WAN port, 4 port 10/100 switch for the LAN, smaller form factor (which is important in a colo cabinet) and still the very easy to use Netopia management interface. These devices were introduced back in March 2003, so they’ve had a good amount of time to update the firmware and make them stable systems. And firmware updates are always free. Which is nice.
I was able to pick one up off eBay for $75 shipped and when it arrived (and got a correct power supply as the one sent to me was for a mobile phone or something – ALWAYS label your power supply with what it goes to) I was pleasantly surprised at the feature set of this new device.
A word about the 3300 line; Back in September 2001 purchased Cayman systems and these devices are actually borne of that line of Cayman dsl modems/routers. So to directly compare them and their performance with the R-series isn’t exactly right on, but I’m going to choose to beieve it’s close enough.
So, it turns out that based on specs alone, this little box should kick butt. The processor families are probably not the same (see above para), but the R9100 has a 33mhz cpu with 4MB ram and the 3386-ENT has a 168mhz cpu with 8MB ram. I’m hopeful that translates into much better performance.
It turns out to be true. I get the router installed and configured for VPN access, then connect to the box from my PowerBook G4 over my FIOS line at home. It took about 5 minutes to set that up. 5 mintes. It took me more than 5 minutes to just to get the right docs open for the NetScreen. Once connected, I was able to easily connect to ip addresses of devices on that backside of the network and work just like I was there connected right up to the LAN. Exactly like a VPN is meant to work.
Performance testing
I’ve found that the best way to easily test the speed of a link is run a Timbuktu (more Netopia!!!) file transfer. It’s always been the most efficient and also shows you nice data rate numbers on how fast things are going. My FIOS line at the house is a 15mbit down/2mbit up connection, so the best thing to try to max out the system would be to pull a file off a box through it’s backside IP.
Trying that I got about 3.5mbit throughput. Pushing a file up to the server, I got about 210K which is essentially maxing out the upstream speed of my FIOS. Still 3.5mbit is pretty darn good. And I was ssh’ed into another box at the same time and didn’t notice any delays or higher latencies in typing or output from top.
Before I did all this, I setup our cacti system to poll the 3386 for both the throughput on the WAN port and the current cpu usage.
So you don’t have to go searching yourself, the SNMP OID for current CPU usage on any Netopia router is: .1.3.6.1.4.1.304.1.3.1.3.1.0
When I was transferring the big files to/from the servers, apparently the 3386 was haulin the chili:
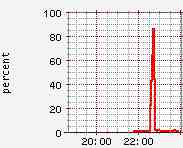
so, not a high-end NetScreen 208 or Cisco VPN concentrator, but a very good performer for a sub-$100 router that is easy to setup.
Other notes
Looking through the screens on this box shows a surprising amount of breadth in feature-sets for such a small device. (make sure you update to the latest firmware)
- VRRP for handling redundant gateways
- QoS – called Prioritize Delay Sensitive data in the interface. Either on or off, but still a nice touch in being able to make sure your VoIP traffic doesn’t get the jitters.
- NTP client settings and update frequency
- WAN link rate limit, in case for some strange reason (which I have encountered), you want to go slower.
- Stateful Inspection of packets to ward off certain types of IP attacks.
- Local NAT (called IP passthrough). allows you to use the WAN IP of the device inside the LAN. Useful for deploying servers internally and providing external access without having to reconfigure hostnames/IP addresses in applications.
- Diffserv for creating specific QoS rules.
- VLAN support for LAN side
- MultiNAT for when your ISP gives you a static 8-IP subnet and you want to implement some interesting routing.
- syslog support
Again, these are not all deeply configurable like a Cisco or a NetScreen, but having the basic features of some of these technologies can sometimes really save your bacon when a client wants something a bit unorthodox.
Overall, I’m pretty happy with the device and I’m waiting on another to arrive from an eBay seller. I hope this is the start of another beautiful friendship with our friends from Netopia (I mean Cayman, wait, Netopia. Right?)